The Internet of Things (IoT) is evolving rapidly, with several new technologies and innovations expanding its capabilities across industries. These technologies focus on improving connectivity, enhancing security, reducing latency, and enabling intelligent, data-driven applications. Here are some of the latest technologies related to IoT:
1. Low-Power Wide-Area Networks (LPWAN)
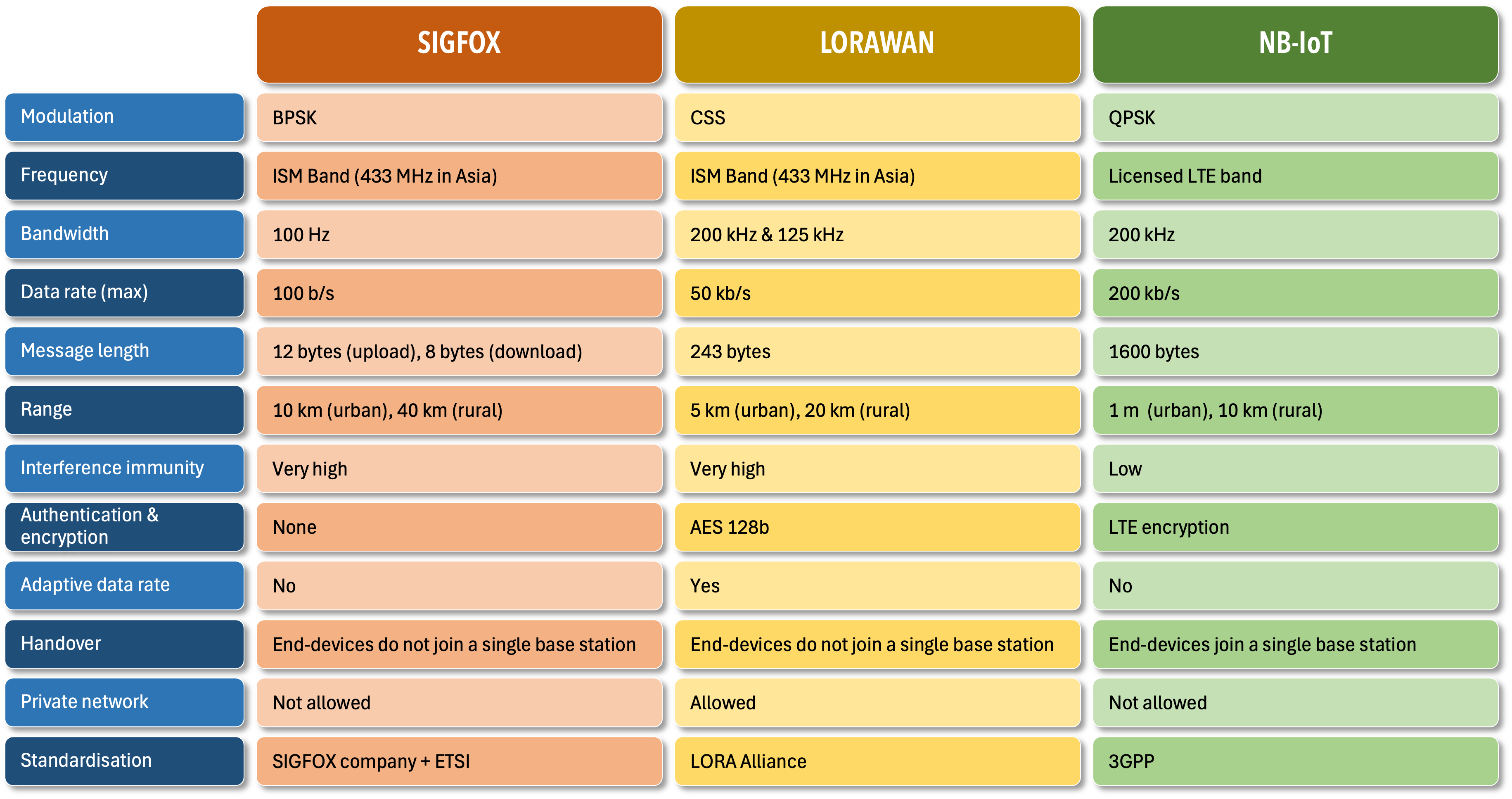
Low-Power Wide-Area Network (LPWAN) technologies like LoRaWAN, NB-IoT, and Sigfox are specifically designed for long-range, low-power IoT applications, making them ideal for connecting battery-operated devices across vast geographic areas. In smart agriculture, LPWAN enables precision farming by connecting sensors in rural and remote areas for tasks such as irrigation management and crop monitoring. For smart cities, LPWAN supports low-bandwidth applications like smart parking systems, environmental monitoring, and waste management solutions. Additionally, LPWAN is extensively used in asset tracking, ensuring efficient monitoring of goods across logistics and supply chains, offering benefits such as long battery life and reduced operational costs.
2. Edge Computing and MEC
Edge computing processes data closer to its source, at the network edge, rather than relying on centralized cloud servers. This approach minimizes latency and reduces bandwidth consumption, resulting in faster and more efficient IoT systems. It supports real-time processing, enabling immediate analytics and decision-making essential for applications like autonomous vehicles, smart grids, and industrial IoT (IIoT). By significantly lowering latency, edge computing is critical for time-sensitive IoT applications, such as remote surgery, AR/VR, and real-time traffic management. Furthermore, its decentralized nature alleviates the burden on centralized cloud infrastructures, enhancing the resilience and scalability of IoT networks.
Mobile Edge Computing (MEC) is a specialized form of edge computing tailored for mobile networks, particularly 5G. It places computing resources at the edge of cellular networks, bringing processing power closer to mobile users and devices. This architecture supports low-latency IoT applications, making it ideal for use cases such as connected vehicles, industrial automation, and remote health monitoring. Additionally, MEC enhances network efficiency by processing data locally, reducing the need for backhaul to centralized cloud systems, optimizing bandwidth utilization, and lowering operational costs.
3. Artificial Intelligence of Things (AIoT) and TinyML
AIoT merges Artificial Intelligence (AI) with the Internet of Things (IoT), enabling devices to autonomously analyze data and make intelligent decisions. This integration makes IoT devices smarter and more self-sufficient, paving the way for advanced automation and enhanced data analytics. In industries such as manufacturing and utilities, AIoT facilitates predictive maintenance by anticipating equipment failures and triggering preventive actions, reducing downtime. For smart cities, AIoT optimizes real-time traffic management, waste collection, energy efficiency, and public safety. In the home, AIoT enhances the capabilities of intelligent devices, allowing them to learn from user behavior and improve energy usage, security, and overall convenience.
TinyML involves deploying machine learning models on low-power, resource-constrained IoT devices, enabling them to perform AI-based inference locally without relying on cloud connectivity. This technology offers energy efficiency by operating on battery-powered devices in remote locations, allowing data processing and decision-making directly at the edge. With real-time decision-making capabilities, TinyML accelerates response times, which is crucial for applications such as smart agriculture, wearable devices, and industrial sensors. Additionally, TinyML provides cost-effective AI solutions by reducing the reliance on cloud infrastructure and bandwidth, making AI processing more affordable and scalable.
4. 5G & 6G Mobile for IoT
5G serves as a transformative enabler for advanced IoT applications, leveraging its high bandwidth, ultra-low latency, and capacity to support a massive density of connected devices. This next-generation network technology unlocks innovative possibilities across sectors such as autonomous vehicles, smart cities, and industrial automation. By supporting millions of IoT devices per square kilometer, 5G facilitates Massive IoT (mIoT) applications, making it ideal for smart cities, agriculture, and logistics. Its Ultra-Reliable Low-Latency Communications (uRLLC) capability enables real-time control systems critical for autonomous vehicles, robotics, and healthcare. Additionally, 5G’s Enhanced Mobile Broadband (eMBB) provides the high bandwidth necessary for data-intensive IoT use cases, such as video surveillance and AR/VR applications.
Although 5G deployment is still ongoing worldwide, research into 6G networks is already progressing, aiming to enhance IoT connectivity and capabilities further. With promises of higher speeds, lower latency, and improved support for massive IoT ecosystems, 6G is set to revolutionize IoT applications. It will deliver sub-millisecond latency, enabling advanced real-time, high-bandwidth applications such as fully immersive AR/VR experiences, real-time AI processing, and holographic communications. Additionally, 6G will provide ubiquitous connectivity, reaching remote and hard-to-access areas, thus supporting critical use cases like smart agriculture, disaster management, and environmental monitoring.
5. IoT Security Innovations
Security is one of the biggest challenges in IoT, and new technologies are emerging to address these concerns.
Blockchain technology is increasingly being integrated into IoT systems to enhance security and protect communication and transactions between devices. By creating secure and immutable records of transactions, blockchain ensures data integrity and privacy, reducing the risks of tampering or breaches. In supply chain management, blockchain-based IoT solutions improve transparency by verifying the authenticity and traceability of goods and materials, ensuring reliable and accountable operations.
Zero Trust Security operates under the principle that no device or network segment should be trusted by default, regardless of its location within the network perimeter. This approach mandates strict verification for all devices and data packets, enhancing IoT security by preventing unauthorized access. Through microsegmentation, IoT networks are divided into smaller, isolated segments, effectively containing potential threats and minimizing the impact of security breaches on critical infrastructure and enterprise networks.
6. Digital Twin Technology
A digital twin is a virtual representation of a physical asset, system, or process that mirrors its current state in real time, enabling monitoring, simulation, and optimization. In Industrial IoT (IIoT), digital twins are widely used across industries like manufacturing, energy, and construction to enhance performance, predict maintenance requirements, and boost operational efficiency. For smart cities, digital twins empower planners to simulate and evaluate the potential impacts of infrastructure changes, such as traffic management adjustments or new public transport systems, before implementation. In healthcare, digital twins create personalized models of patients, facilitating tailored treatment plans and enabling real-time health monitoring for improved outcomes.
7. IoT Interoperability Standards and Protocols
To address the challenges of interoperability, new standards and protocols are being developed for seamless communication across different IoT ecosystems.
Matter Protocol (formerly Project CHIP) is a universal IoT connectivity standard developed to unify smart home devices across different ecosystems. Backed by industry leaders like Google, Amazon, and Apple, Matter establishes a common framework that enables seamless interaction between smart devices, regardless of the manufacturer. This standard addresses the critical challenge of interoperability, ensuring devices from various vendors can work together effectively. By simplifying device setup and enhancing user experiences, Matter significantly improves the convenience and functionality of smart home ecosystems.
Thread Protocol is a low-power, IPv6-based wireless networking protocol specifically designed for IoT applications. It allows devices to form secure and reliable mesh networks, facilitating direct communication between them. This enhances network reliability and reduces latency, making Thread particularly suitable for smart home and building automation. Supporting low-latency applications like smart lighting, HVAC systems, and security cameras, Thread ensures rapid response times for critical systems, delivering more efficient and responsive IoT solutions.
8. Green IoT and Energy Harvesting
Green IoT emphasizes reducing the environmental footprint of IoT devices by incorporating energy-efficient designs and energy-harvesting technologies. These advancements enable IoT devices to operate without traditional batteries, instead collecting energy from ambient sources such as solar power, electromagnetic waves, or vibrations. This approach supports long-term sustainability, allowing devices to function autonomously for extended periods while minimizing waste and resource consumption.
In smart agriculture, energy-harvesting sensors can be deployed in remote or hard-to-reach areas, collecting crucial environmental data such as soil moisture and weather conditions. This eliminates the need for frequent battery replacements, reducing maintenance efforts and costs while promoting sustainable farming practices.
